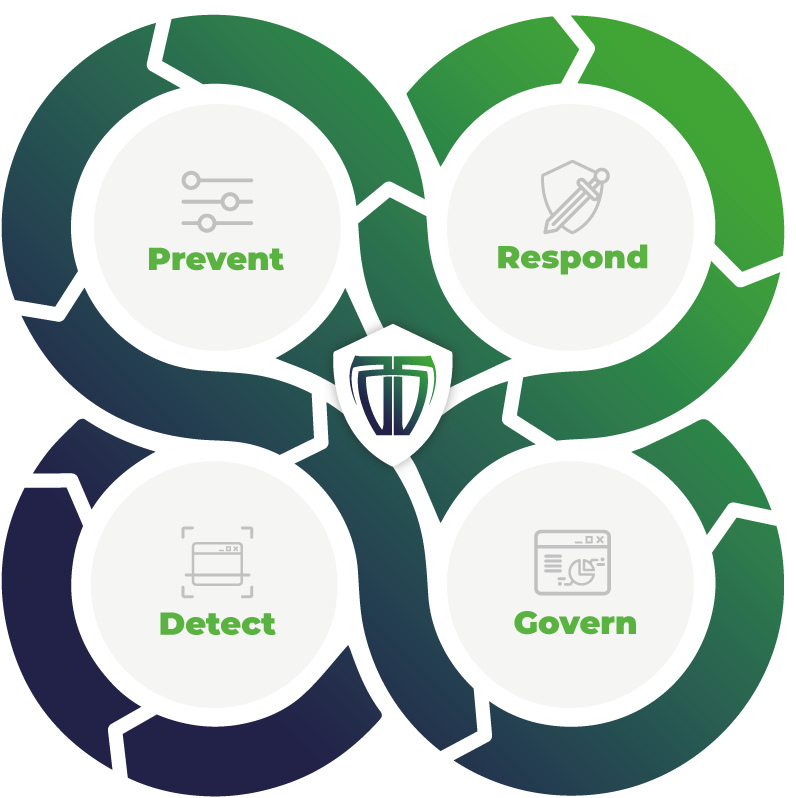
Secure your digital valuables and continuously improve your security
We can help you by responding to potential risks, as well as continuously improving the process in accordance with our tested 360-degree method. Or are you lucky enough never to have security problems?