
During incident response cases, determining how an adversary gained access to the IT infrastructure is not always as clear cut as “It was colonel Mustard in the remote access VPN solution with the leaked user credentials”. Instead, the Adversary trail may lead to an application or device, which “magically” led to initial access, privilege escalation or lateral movement. The “magic” in these cases is the exploitation of a vulnerability residing in an application or device.
With the vast number of applications and devices in use today, it is impossible to be aware of all vulnerabilities. Being able to quickly identify relevant vulnerabilities, specifically those with a high chance of exploitation, will enhance the abilities of Incident Response teams to quickly respond and minimise impact.
EPSS
Common Vulnerability Scoring System (CVSS) is a well-known system, developed by FIRST, which is used to score the characteristics and severity of registered vulnerabilities. CVSS is a powerful metric to score the potential impact of a vulnerability, but not the likelihood of that vulnerability being exploited. That is where the Exploit Prediction Scoring System (EPSS), also developed by FIRST, comes into play.
EPSS provides a system to score the chance a vulnerability will be exploited in the next 30 days for a given date. It produces a probability score of a rational number between 0 and 1. The higher the score, the greater the probability that a vulnerability will be exploited. This score is based on the CVSS score and data retrieved from the following sources:
- MITRE’s CVE List – Only CVEs in the “published” state are scored
- Text-based “Tags” derived from the CVE description and other sources talking about the vulnerability
- Count of how many days the CVE has been published
- Count of how many references are listed in the CVE
- Published Exploit code in any of: Metasploit, ExploitDB and/or Github
- Security Scanners: Jaeles, Intrigue, Nuclei, sn1per
- CVSS v3 vectors in the base score (not the score or any subscores) as published in the National Vulnerability Database (NVD)
- CPE (vendor) information as published in NVD
- Ground Truth: Daily observations of exploitation-in-the-wild activity from AlienVault and Fortinet.
More about EPSS and the data sources and models used, can be found on the website of FIRST for EPSS: https://www.first.org/epss/
Vulnerability Explorer
Although the initial use-case for developing EPSS was the prioritization of patches during a patch management process, T-CERT (Tesorion Computer Emergency Response Team) believes it can also be used to identify potentially exploited vulnerabilities during an incident response engagement. To leverage the power of EPSS, T-CERT created the Tesorion Vulnerability Explorer application. This easy-to-use application enriches the NIST NVD CVE database with the corresponding CVSS and EPSS scores as well as the CISA Known Exploited Vulnerabilities (KEV) catalog. Using the Common Platform Enumeration (CPE) notation system, you can easily filter for a specific product.
Hopefully you are still with us, because that’s quite a few abbreviations, systems, and frameworks for such a short paragraph! More information regarding those can be found in Chapter “Systems and frameworks used”.
Sneak peek
The goal of the Tesorion Vulnerability Explorer is finding vulnerabilities for a given application and enriching it with information to score the probability of exploitation. The search bar at the top of the Tesorion Vulnerability Explorer allows you to search for a specific CPE-string. In the example below a search is performed for vulnerabilities in any version of the Atlassian Confluence product by providing the following CPE query to the Tesorion Vulnerability Explorer:
• cpe:2.3:a:atlassian:confluence*
| Element | Description |
| cpe:2.3 | Schema version |
| A | Part – “a” is the abbreviation of Application, Other options are “o” for operating system and “h” for hardware |
| Atlassian | Vendor |
| confluence | Product |
| * | A wildcard is used for the fields: version, update and edition |
Table 1 – The CPE filter explained
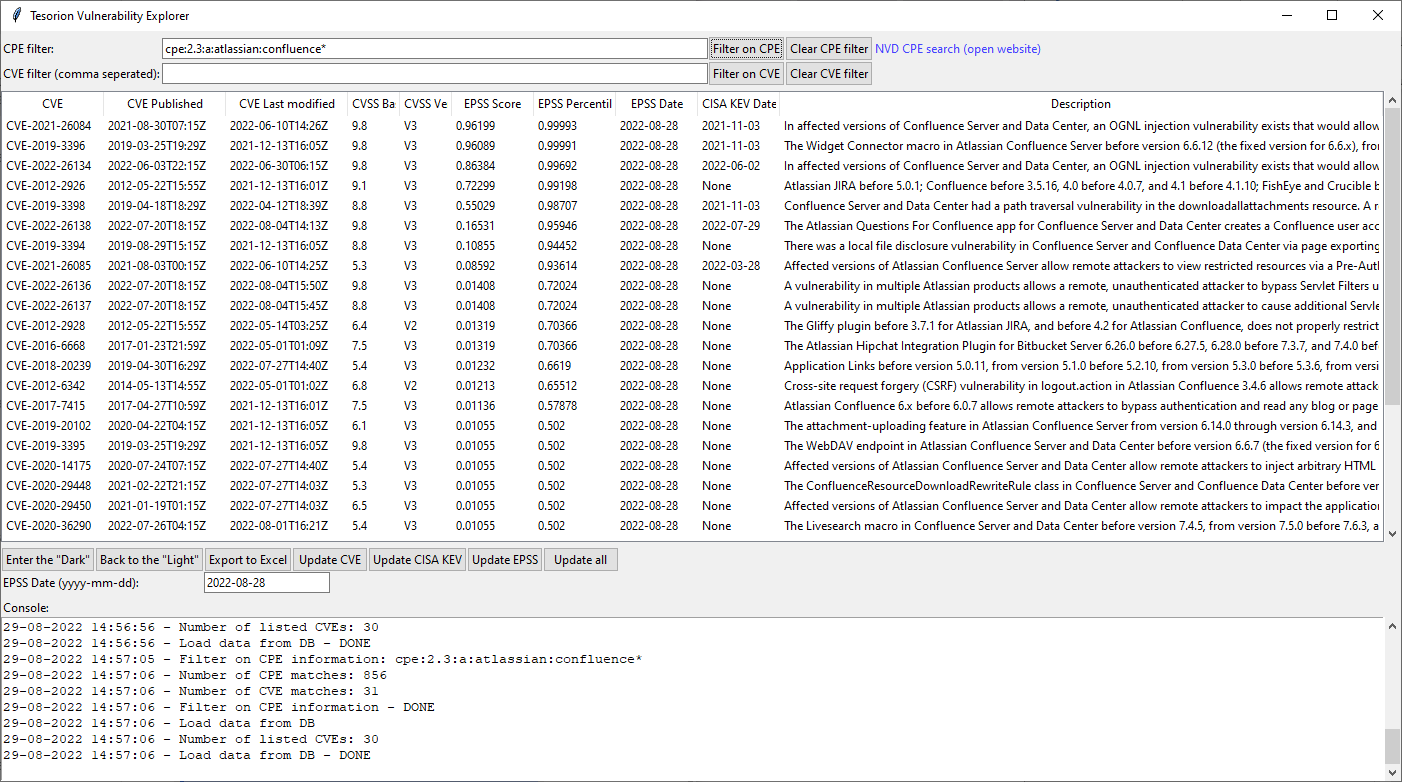
Figure 1- Example usage of the Tesorion Vulnerability Explorer
The result is displayed in the figure above. Based on the console output located at the bottom of the screen, we can determine there are 856 matching records for the given CPE-string. The 856 matching records have 31 related vulnerabilities. Of those 31 vulnerabilities, we have 30 available in the application as we only import NVD information made available from 2010 and onwards.
When sorting by EPSS Score, CVE-2021-26084 comes out on top. This indicates that for an exploit of the Atlassian Confluence server, this is the most obvious vulnerability to be aware of during your incident response. Of course, this example was simplified, lacking critical details such as the current patch level of the Confluence server.
To quickly gain more detailed insights regarding the specific vulnerability, a detail screen can be opened by double clicking the entry. An example can be seen in the figure below.
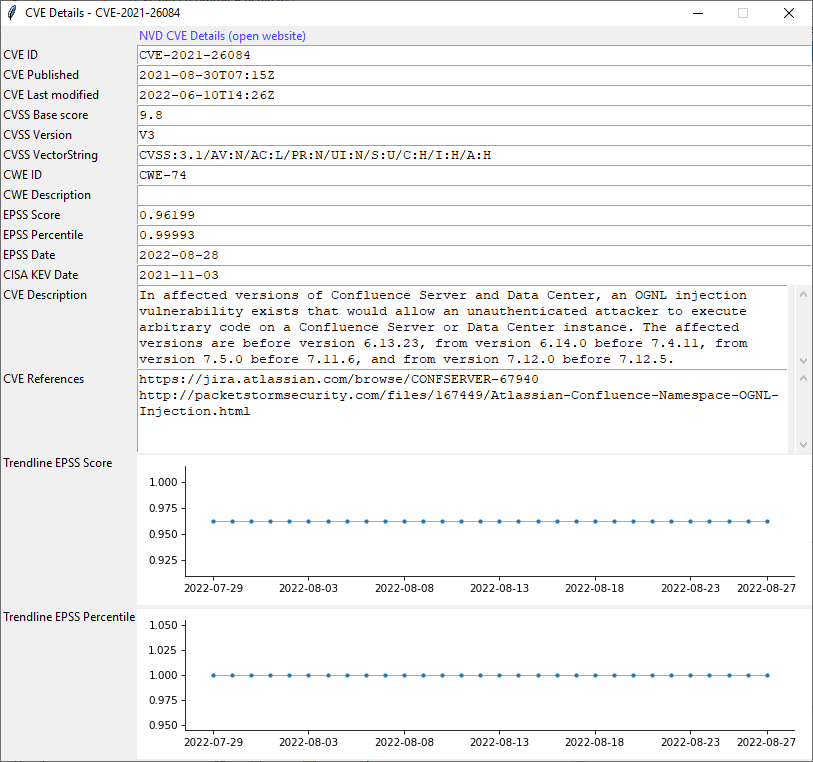
Figure 2 – The detail screen for a specific vulnerability
This detail screen provides more information related to the CVE, which exists of the following elements.
| Element | Description |
| CVE information | General information like the CVE ID, publication date and a link to the NVD website for more vulnerability details. |
| CVSS Base score | The score assigned by NVD indicating the expected impact. |
| EPSS Score | The score calculated with EPSS. |
| EPSS Percentile | The percentage of vulnerabilities with a lower EPSS Score as the current vulnerability. |
| EPSS Date | An important part of EPSS is the date. The date provided here is the date used to calculate the EPSS Score and EPSS Percentile in this overview. |
| CISA Date | The date since when CISA sees public exploitation for the vulnerability. If no date is given, CISA has not listed the vulnerability in their Known Exploited Vulnerabilities Catalog. |
| Trendline | For both EPSS Score and EPSS Percentile, a trendline for the last 30 days is given. |
Table 2- Description of elements of the vulnerability details screen
Note: the Tesorion Vulnerability Explorer application is currently a work in progress and is not publicly available yet. A second blog, for a more in-depth explanation of the application has been published and in the mean time as well as a public release of the application!
Systems and frameworks used
The Tesorion Vulnerability Explorer gets its power from combining different scoring systems and frameworks. More information about these systems and frameworks can be found in the overview below, including links to their respective websites:
- EPSS – Exploit Prediction Scoring System – An open, data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild. This system is built and maintained by FIRST.
- CVE – Common Vulnerabilities and Exposures – The registration system for keeping track of known vulnerabilities. Tesorion Vulnerability Explorer uses the enriched dataset set from the NIST NVD, which is built upon and fully synchronized with the CVE List.
- CVSS – Common Vulnerability Scoring System – An open framework for communicating the characteristics and severity of software vulnerabilities. The framework is developed and maintained by FIRST. The scores for individual CVE’s are assigned by NIST NVD.
- CPE – Common Platform Enumeration – A structured naming scheme for information technology systems, software, and packages. The CVE information from the NIST NVD is enriched with the impacted products in the CPE format. Tesorion Vulnerability Explorer leverages this format, to select vulnerabilities for specific products.
- CISA KEV catalog – CISA Known Exploited Vulnerabilities catalog – CISA keeps track of vulnerabilities identified as known to be exploited in the wild.












