
Last week, we published a blog post on our analysis of the new ThunderX ransomware. In this blog post we also announced a free decryptor for ThunderX victims, available through the NoMoreRansom website. Since then, our decryptor has been helping victims of ThunderX to recover their files for free.
Soon after a tweet that ThunderX could be decrypted and our publicly available free decryptor, a new version of ThunderX appeared, with a different name: Ranzy Locker.
In this blog post, we hilight some of the differences between the original ThunderX and Ranzy Locker. Fortunately for Ranzy Locker victims, it is in some cases still possible to recover their data without paying the ransom, although this requires a more bespoke approach.
Ransom note differences: what’s in a name?
First of all, as some ransomware is distributed through a Ransomware-as-a-Service (RaaS) model, it can be hard to tell whether differences between variants are caused by a single operator making (evolutionary) changes, or multiple operators each using their own configuration. We are not certain which is the case for the differences we describe below, but considering the relatively small scale of ThunderX, we would not be surprised if the authors are also the sole operators of ThunderX and Ranzy Locker.
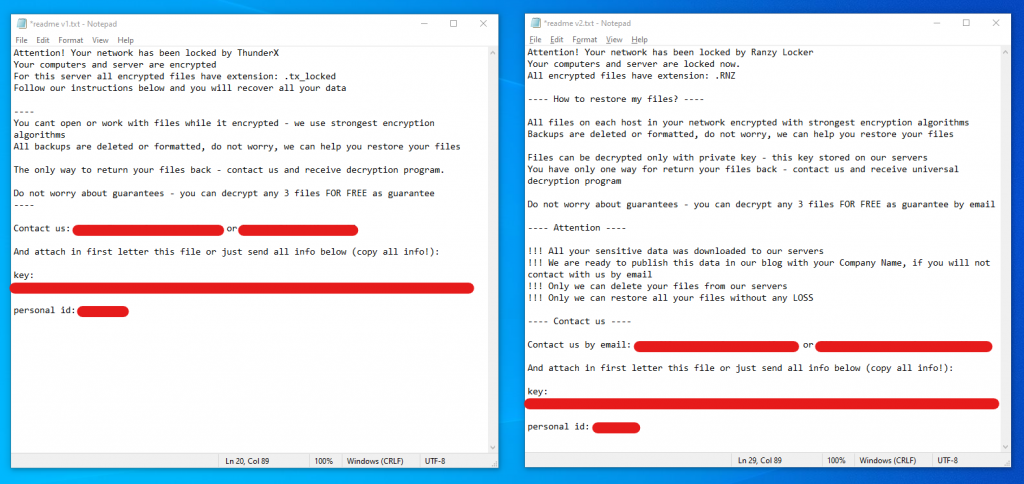
If we look at the ransom notes for ThunderX and Ranzy Locker, they are clearly very similar. For example the claims of using ‘strongest encryption algorithms’ and (supposedly) being the only ones able to recover the encrypted files.
The change of the name from ThunderX to Ranzy Locker (and the accompanying file extension) of course stands out. Reputation is an important aspect of the ransomware business: if victims believe there is a reasonable chance their files can be decrypted for free, either now or in the near future, they might be less inclined to pay the ransom. Of course this is just speculation, but that might be one of the reasons behind the change in name from ThunderX to Ranzy Locker.
Another small, but important, difference is that the ransom note for Ranzy Locker also mentions “All your sensitive data was downloaded to our servers” and “We are ready to publish this data in our blog with your Company Name, if you will not contact with us by email”. This of course is a common threat these days with ransomware operators to further pressure victims into paying. We are not currently aware of any leaked data from Ranzy Locker victims being published. We do know the ransomware binary itself does not seem to contain functionality to leak data, so if the operators actually obtain sensitive data from their victims, this must happen through another, separate process on the infected machines.
Code differences and similarities between ThunderX and Ranzy Locker
When we compared the code of Ranzy Locker to that of ThunderX, we encountered just a very small number of changes. Apart from the name (which is really more of a configuration-change loaded from encrypted strings in the resources), the main difference is (unfortunately) in the cryptography. The authors have clearly been paying attention and changed their code in such a way that the approach we used in our free decryptor for ThunderX does not work for Ranzy Locker. However, not all hope is lost as decryption is still possible in some cases (more on that below).
Furthermore, in our previous blog post [1] we described a couple of interesting bugs in the ThunderX code. These bugs are both still present in Ranzy Locker, but another rather curious bit of code has been added: Ranzy Locker generates an RC4 encryption key through the Windows Cryptography Provider API, but does not seem to use it at all. We expect this to either be a ruse by the authors, or (perhaps more likely) a remnant of an older attempt to update the encryption code that was abandoned but not completely removed.
Decryption without ransom
Fortunately, decryption of files encrypted by Ranzy Locker without paying the ransom is sometimes still possible. Even though the more generic approach we used for our ThunderX decryptor on NoMoreRansom no longer works, the implementation of Ranzy Locker’s cryptography still contains some interesting bugs that can allow recovery of encrypted data.
We have developed tools that allow our CERT team to decrypt files encrypted by Ranzy Locker in some cases. However this requires some additional work specific to each victim that we unfortunately can not offer through a free decryptor. If you have been hit by Ranzy Locker and would like to discuss whether decryption without paying the ransom is possible, please contact our CERT team.
Conclusion
Many ransomware families see rapid evolution as malware authors strive to stay ahead of detection (and in some cases decryption) efforts by security researchers. It is therefore not surprising to see a new and updated variant of ThunderX (albeit with a different name) so soon after the first version: as soon as it becomes well-known that victims can recover their files for free, their motivation to partake in the ransomware business model quickly vanishes.
Now that it is known that victims of the nearly identical Ranzy Locker may also be able to recover their files without paying, the code and name might change again. In the mean time: if you have been hit by Ranzy Locker, you can contact our CERT team to discuss how we may be able to help you recover your data without paying the ransom!
Indicators of Compromise
SHA256 van de Ranzy Locker binary die in deze analyse gebruikt is: f49e706389b4d4bd83cf567ef97fa89fe0074044ba3c7f2b42fc8d4a4162fefc












