Ransomware remains a major cyber threat for both businesses and consumers to this day. Even though many big names already exist in ransomware land, new families still frequently appear in the wild. We recently found such a new family called Judge. BleepingComputer posted about this family, linking to a tweet by xiaopao.
We decided to investigate this ransomware, and in this blog post we discuss our findings. The blog post starts with a general overview of the ransomware. Furthermore, we will mention some curious details and dive into how it encrypts files. Finally, we also announce a free decryptor for this ransomware. The decryptor will be available through the NoMoreRansom initiative soon to help victims at no charge.
Overview
The Judge ransomware is written in a .NET language, most likely Visual Basic. It starts with creating or checking a mutex named “vYtzIm0SDgeCYX5eq8g7” to prevent multiple instances from running in parallel. It then performs some checks to determine whether it is running inside a sandbox, kills blacklisted processes and deletes system restore points. After these tasks are completed, the cryptography is initialized, and files are encrypted.
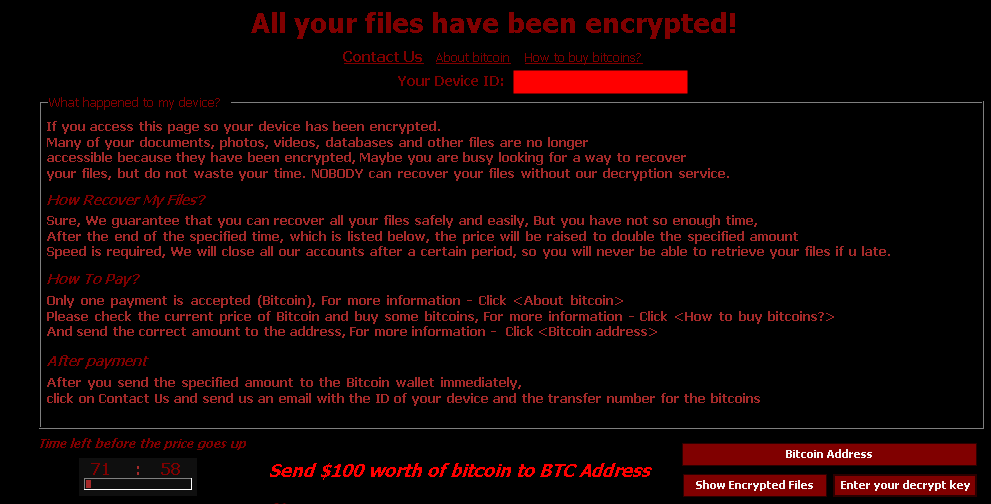
A curious detail about Judge is that the ransomware is both encryptor and decryptor. As we can see in the screenshot below, a button called “Enter your decrypt key” is located at the bottom right of the window. This button opens a window that allows the victim to enter a password and decrypt all files instantly. Instead of this approach, it is more common for a ransomware to offer a decryptor separately after the victim has paid, instead of just the key or password.
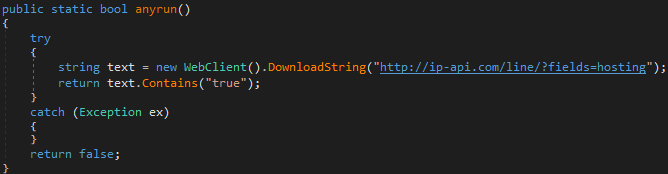
Another interesting detail is the anti-sandbox checks that the ransomware performs. It checks common things such as CheckRemoteDebuggerPresent and artifacts on the infected system that indicate VMware, VirtualBox or Sandboxie. A more interesting anti-sandbox check is shown in the screenshot below. The name of the function suggests that the ransomware is trying to detect whether it is being run in the ANY.RUN sandbox. The IP-API query in this case returns true if the victim’s system is located in a datacenter or hosting network. The ransomware probably uses this to check whether it is not running on a server.
File encryption
The Judge ransomware encrypts files using the AES-256 algorithm in CBC mode. It encrypts every file whole in blocks of 4KiB, and therefore, it can take a while to encrypt large files. Encrypted files get a file extension of the form: “[[email protected]].judge” and do not have a footer containing information about the encryption.
Upon encryption, the ransomware generates a password to derive the key and IV for AES from, and every file is encrypted with this same key and IV. The victim needs this password again to decrypt his files later. The attacker however must be able to provide this password to the victim. It turns out that the ransomware sends the password in plain text to the command & control server of the attacker, combined with a value used to identify the victim. Most ransomware attackers commonly provide a private value for decryption after the victim sends its public one. However, this ransomware is only using symmetric encryption, and therefore, it is not possible to do this.
A free decryptor
Based on our analysis of the Judge ransomware we have come to the conclusion that we can decrypt all (non-corrupted) affected files without paying the ransom. We have built a decryptor that we are providing to victims free of charge. The decryptor is available for download via the NoMoreRansom initiative.
Indicators of Compromise (IoC)
| Indicator | Value |
| SHA256 of ransomware | 73ffa4ad8f7c49254febc4f90456a675905b173204a5450259ac3af483eb7a2f |
| SHA256 of ransomware (unpacked) | ed6688508433b68b84ac86fbe6c9e20c68f0d6a925fe4d16a3896013efed00a9 |
| Command & control hostname | fedex[.]tokyo |